Notebook Computer Care Tips
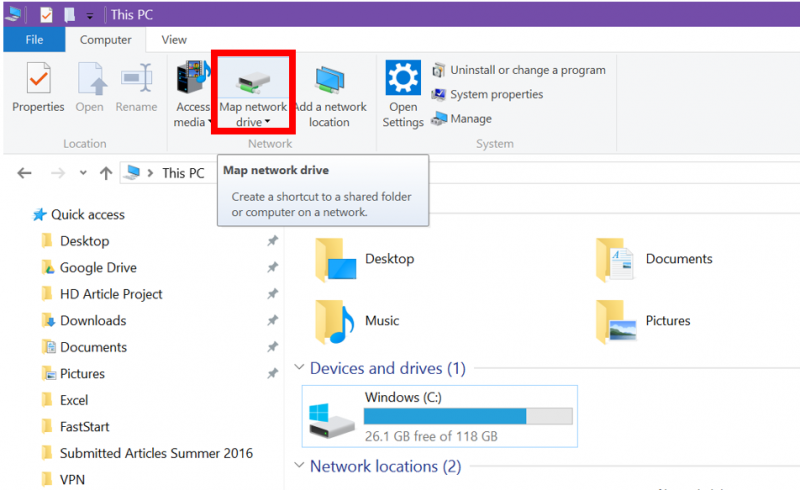
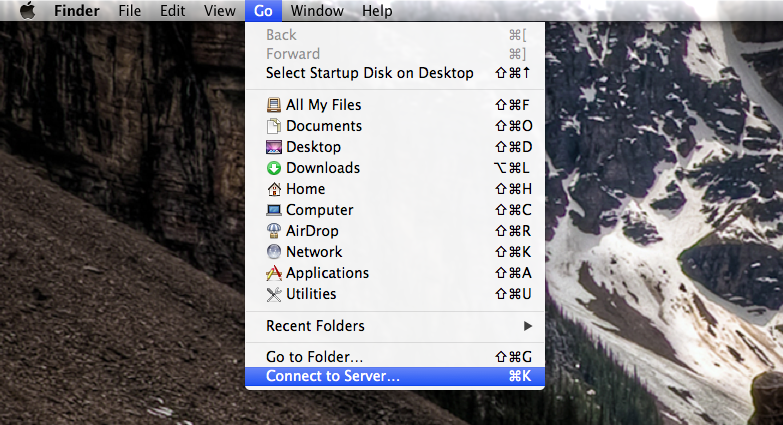
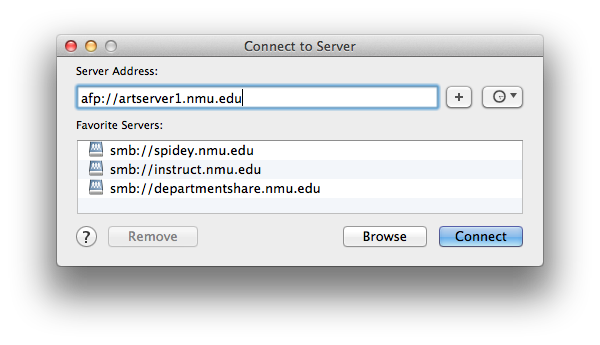
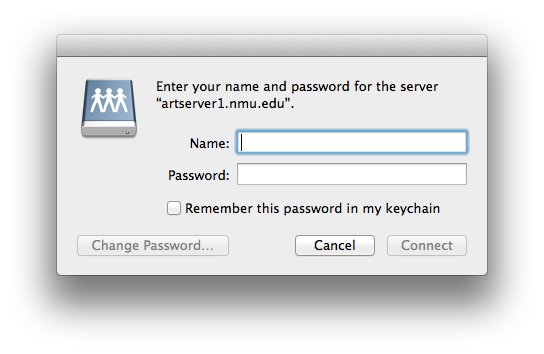
Documentation
Notebook computers are precision machines that require a bit of careful handling. Though the ThinkPad computer is designed and tested to be a durable notebook computer that functions reliably in normal work environments, you need to use some common sense in handling it.
Below is a list of things you can do to prevent possible damage to your notebook computer.
- Turn off all attached devices.
- Turn off the computer and close the LCD.
- Unplug all external cables, devices, and cords connected to your computer before you relocate it.
- Make sure all computer doors and covers are closed.
- Use a quality carrying case that provides adequate cushion and protection.
- Shut your computer off before transporting it.
- Back up your files often in case of damage.
- Be sure to keep your machine up to date to avoid software problems in the future.
- Make sure your computer is password protected.
- Regularly scan for viruses. Viruses can hide in places you wouldn’t expect and can slow down your machine without you realizing it.
- Always make sure that software you download has come from a reliable source to prevent viruses.
- Keep canned air handy to dust the machine regularly.
- A re-image isn’t a bad thing! Re-imaging your machine at the beginning of the year can help keep your machine updated and can better prepare your machine for new class-related software.
Below is a list of things you should not do.
- Subject your computer to physical punishment, such as dropping or bumping.
- Place heavy objects on your computer.
- Spill or allow liquids into your computer.
- Pack your computer in a tightly packed suitcase or bag. The compression might cause internal damage.
- Disassemble your computer.
- Scratch, twist, hit, or push the surface of your computer display.
- Place any objects between the display and keyboard or under the keyboard.
- Pick up or hold your computer by the display. When picking up your open computer, hold it by the bottom (keyboard) half.
- Turn your computer over while the AC Adapter is plugged in. This could break the adapter plug.
- Store your computer where the temperature is below 41° F or above 95° F (5° C and 35° C).
- Lend your computer to anyone while you are not present.
- It is not recommended to use your machine anywhere near sand, dirt, gravel, etc. Sand can get into small places in the machine and could cause problems.
- When cleaning the keyboard it is not advised to remove the keys yourself. It is possible to break a small piece on the key that holds it to the keyboard.
- Do not torrent software! While file sharing may not inherently be bad, it is sometimes used illegally and can make your machine vulnerable to a lot of different viruses!